GovWare 2025 saw a rare convergence behind closed doors. Blackpanda, Lenovo, and SentinelOne co-hosted an exclusive CXO Roundtable for cybersecurity and IT leaders from across Asia, centered on one pressing theme: “First to Last Line of Defence — Building Enterprise Resilience.”
As cyberattacks grow in sophistication and frequency — especially across AI-enabled, hyperconnected environments — enterprise leaders are rethinking what true resilience looks like. The discussion, anchored by Blackpanda Founder and CEO Gene Yu, together with partner insights from Lenovo and SentinelOne, offered a blueprint for a new era of security integration: from endpoint to supply chain, from readiness to recovery.
Cybersecurity as Human Conflict
Opening the roundtable, Gene Yu, a former U.S. Special Forces officer turned cybersecurity entrepreneur, reframed cybersecurity as a human-on-human conflict rather than a purely technological one.
“Technology is only part of the equation,” Yu noted. “Real resilience is built when humans — defenders and decision-makers — are trained to respond under pressure. That’s where readiness becomes reality.”
Yu’s military candour cuts through industry jargon. His philosophy, shaped by years in the field, reframes resilience not as a checklist but as a matter of survival. It’s the same principle behind Blackpanda’s Readiness → Response → Recovery framework — a three-tiered model that integrates proactive preparation, rapid crisis intervention, and post-breach financial protection through insurance.
He described Blackpanda as the “hedge” in enterprise cyber strategy — a fail-safe partner ready to respond when others are at capacity. With underwriting authority from Chaucer, a Lloyd’s of London syndicate, Blackpanda uniquely fuses technical response expertise with insurance capacity — underwriting up to US$10 million per policy across Asia.
This hybrid “insurance-backed incident response” model enables enterprises to more safely depend on emergency access to responders, as Blackpanda’s insurance can contract and pay for other trusted and partnered global incident responders in case Blackpanda is at full capacity — rather than waiting in line when a major breach wave hits.
Incident Response as Insurance
Blackpanda’s flagship product, IR-1, exemplifies this philosophy: an incident response assurance subscription based on insurance principles — essentially incident response as a policy — offering incident response at 10-20x less than traditional retainers.
“Traditional consulting models break under surge conditions because they are incentivised to run at maximum capacity, being paid only after the work is complete,” Yu said. “The insurance business model provides predictable, upfront recurring revenue that enables superior resource allocation and planning of our responders’ bandwidth. We’re here so that enterprises never have to hear the words: ‘We’re fully booked.’”
In a strategic integration, Lenovo customers now receive up to 20% off Blackpanda’s Lloyd’s of London-backed cyber insurance, enabled by Lenovo’s secure supply chain and ThinkShield ecosystem — a partnership designed to make resilience more accessible across Asia’s enterprise landscape.
Unified Platform: From Readiness to Recovery
The partnership between Blackpanda, Lenovo, and SentinelOne is quietly building what many in the room described as “a new security operating system for the region.”
- Lenovo fortifies supply chain and endpoint trust through ThinkShield, embedding security in product design and procurement.
- SentinelOne delivers AI-driven detection and response at machine speed.
- Blackpanda closes the loop — providing preparatory consulting, emergency response, and cyber insurance coverage.
The combined strategy: a single resilience stack from the first to the last line of defence.
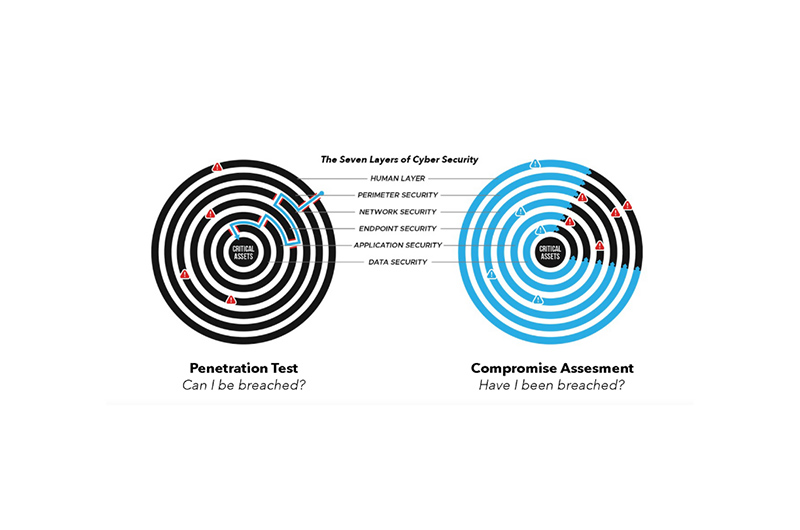
Yu emphasised pre-breach engagement as a critical differentiator. “We train on the same terrain we’ll operate in. Incident response plans and playbooks, or compromise assessments and regular threat-hunting cycles on actual customer infrastructure, are how we build readiness that matters — because it enables our responders to rehearse firefighting on your actual house before the fire occurs,” said Yu. “You can’t outsource readiness; you have to build muscle memory before chaos begins.”
He also noted a growing trend among large enterprises to retain multiple IR firms on standby — mirroring the redundancy strategies long adopted in physical disaster recovery planning.
SentinelOne: AI as a Double-Edged Sword
Representing SentinelOne, executives showcased how the company’s AI/ML heritage continues to shape the future of endpoint protection. Recent acquisitions — including Prompt Security — have expanded the platform’s AI enablement and data-ingestion capabilities, helping analysts reduce alert fatigue and leverage natural language querying to surface relevant threats faster.
The message was clear: as AI accelerates both offence and defence, platform consolidation and automation are no longer optional — they are the only way to stay ahead.
Lenovo: Securing the Supply Chain Frontier
Lenovo’s presentation zeroed in on supply chain resilience — increasingly the most exploited yet under-defended attack vector.
Through its ThinkShield portfolio, Lenovo has developed golden image validation for critical components, embedding security at the design stage. A recent beta deployment highlighted how secure provisioning can now be completed in just 15 minutes per endpoint, illustrating both efficiency and trust at scale.
Given that the average cost of a supply chain breach now exceeds US$4.4 million, Lenovo’s integration of security-by-design principles — with product managers working hand in hand with engineers — marks a tangible shift towards proactive, hardware-level defence.
Emerging Threats and Market Dynamics
Across the discussion, a few unmissable trends emerged:
- AI as the new arms race: Offensive and defensive capabilities are evolving in tandem.
- Edge devices as new gateways: From home IoT to industrial controls, endpoint sprawl is the next frontier for attackers.
- Tech debt as silent risk: Legacy systems and incomplete digital transformations widen exposure gaps.
- OT/IT convergence: Critical infrastructure operators are facing a collision between old systems and new threats.
- Collective defence through intelligence sharing: CISOs called for deeper collaboration across private and public sectors — especially in Singapore, where regulatory momentum is strong.
The Road Ahead: Resilience as Competitive Advantage
As one CISO attendee put it during the Q&A:
“We used to measure cyber maturity by how many tools we had. Now it’s about how fast we can recover.”
That sentiment captures the shift this roundtable embodied. The era of reactive cybersecurity is over. Enterprises are moving toward resilience engineering — an integrated posture where readiness, response, and recovery are not separate functions but a unified capability.
Through partnerships like this, Blackpanda, Lenovo, and SentinelOne are demonstrating what that looks like in practice — a future where cyber resilience is not just a defence strategy, but a business advantage.
Get Future-Ready
Blackpanda helps enterprises across Asia build true resilience — combining incident response assurance, technical expertise, and insurance-backed protection in one integrated model.
➡️ Learn more about IR-1 or speak with our team to secure your organisation’s last line of defence:
About Blackpanda
Blackpanda is a Lloyd’s of London–accredited insurance coverholder and Asia’s leading local cyber incident response firm, delivering end-to-end digital emergency support across the region.
We are pioneering the A2I (Assurance-to-Insurance) model in cybersecurity — uniting preparation, response, and insurance into a seamless pathway that minimises financial and operational impact from cyberattack.
Through expert consulting services, response assurance subscriptions, and innovative cyber insurance, we help organisations get ready, respond, and recover from cyberattacks — all delivered by local specialists working in concert.
Our mission is clear: to bring complete cyber peace of mind to every organisation in Asia, from the first moment of breach through full recovery and beyond.
Frequently Asked Questions
Q1: What makes Blackpanda different from other cyber incident response providers?
A: Unlike most incident response firms, Blackpanda is first and foremost a Lloyd’s of London insurance underwriting company and approaches the delivery of the service from this unique angle. Blackpanda directly assumes risk with its own insurance-like response assurance products. This means we guarantee availability and completion of investigation, containment, and neutralisation of the cyberattack — not just consultancy hours. We’re able to deliver the full post-breach lifecycle that helps organisations get ready, respond, and recover from cyberattacks — all delivered by local specialists working in concert.
Q2: What is the Blackpanda IR-1 product?
A: IR-1 is Blackpanda’s fixed-cost annual subscription that gives your organisation one guaranteed incident response activation per year. It is also referred to as an assurance product in the insurance industry. Instead of paying unpredictable crisis fees on an hourly basis, IR-1 ensures you always have a dedicated response team on standby that is committed to completing a successful outcome of resolving the cyberattack from containment to neutralisation — at the click of a button.
Q3: How does Lenovo’s ThinkShield integrate with Blackpanda’s IR-1?
A: Blackpanda’s IR-1 is a partner to Lenovo’s ThinkShield portfolio. Lenovo enterprise customers may enjoy IR-1 embedded for their entire enterprise as part of their procurement process of Lenovo devices. In addition, any Lenovo customer with IR-1 embedded in its devices may enjoy up to 20% savings on Blackpanda’s comprehensive cybersecurity insurance due to our confidence in our ability to limit damage with our incident response speed of containment.
Q4: How does AI impact considerations with cyber emergency response?
A: While AI-driven detection accelerates defence, attackers are also leveraging AI to automate phishing, data exfiltration, and exploit discovery. The next phase of cybersecurity is about mastering both sides of that evolution. As Blackpanda’s service offerings hyperfocus on incident response only as the core mission of the company, we are constantly iterating and considering implications and applications of AI as part of our incident response solution.
Q5: How can enterprises prepare for faster incident recovery?
A: Adopt a readiness-to-recovery approach: conduct Compromise Assessments, regular Threat Hunting, and other consulting services on actual infrastructure to ensure that your dedicated incident response team is fully rehearsed and familiar with your environment for when the worst occurs.























































.jpeg)
.jpeg)