Cyber Trends for APAC in 2022
2021 was a volatile year for cyber security in Asia with the world experiencing the highest growth in cyber threats to date fuelled largely by developments in attack techniques—ransomware in particular, with ransomware as a service (RaaS) and double extortion techniques gaining prominence.
The rise in attacks comes at a time when the barriers for entry into cyber crime are at their lowest, as threat actors face low risks and unprecedentedly high returns for their efforts. Consequently, cyber incident response providers have been tasked with stepping up to this challenge and staying up to date with the latest techniques and exploits leveraged by the growing number of cyber threat actors.
In light of this, our experts from the Blackpanda Digital Forensics and Incident Response team predict the current pace of cyber crime evolution to persevere in 2022. As “firefighters” combatting the flames on the front lines of cyber crisis, we have drawn upon our experience in the field to predict the top three attack trends that will likely dominate the cyber security landscape in Asia this upcoming year.
1) Ransomware
Ransomware demands reached an all-time high in 2021. In fact, ransomware cost the world USD 20 billion in 2021 and that number is expected to rise to USD 265 billion by 2031.
One of the most prominent attacks in Asian history was also carried out last year. AXA–one of the world’s largest cyber insurance companies—was targeted by a ransomware attack carried out by the cyber criminal gang Avaddon. The attackers were able to steal over three terabytes of files, including client passport details, ID cards, denied reimbursements, contracts, customer claims, payments to customers, bank account information, files from hospitals about fraud investigations, and medical reports that had sensitive information about patients.
Alongside large corporations, digital extortion is increasingly affecting small businesses as well. This trend is predicted to continue in 2022, with new ransomware techniques—such as double extortion—becoming more prevalent.
Growing ransom demands and increased regulation around ransomware payments will make professional incident handlers essential to ensure security and legality in ransomware negotiations. The Charter of United Nations Act 1945 and Autonomous Sanctions Act 2011 and their related regulations already prohibits making funds or assets available to sanctioned organisations. Moreover, Australian authorities have also come up with their own version of a Ransomware Action Plan that prohibits ransom payments, with other APAC countries expected to follow suit.
2) Zero-Day Attacks
Zero-day attacks are set to continue dominating headlines worldwide. This type of attack is caused by criminals exploiting the vulnerabilities that are present in unpatched software, discovering them before software developers become aware of them.
In late August 2021, Hong Kong iOS and Android users visiting a pro-democracy media website were targeted by a zero-day attack which installed spyware and stole data from their devices.
Later in the year, the Log4J Apache vulnerability was exploited on a global scale, affecting upwards of 3 billion devices worldwide. The Log4j zero-day is a clear example of how software vulnerabilities can be unknown until they are widely exploited, and can affect a large proportion of organisations. This means that the only way to mitigate an attack is through improved proactive security controls and rapid incident response.
3) Systemic Risk Events
As we saw last year with the Handa Hospital attack—where attackers were able to infect the facility’s networks thanks to a vulnerability in one of the hospital’s third-party contractors’ VPN—third party dependencies are and will continue to be a weak link in cyber defences. This is because smaller companies are generally an easier target for attackers, and they provide an access point for attackers to reach their larger partners.
Due to their widespread use, managed service and cloud computing providers will continue to be lucrative targets for cybercriminals. For this reason, the fear of the next large-scale systemic risk event—whereby a single event has the potential to impact thousands of businesses— should be at the forefront of everyone’s mind in the cyber security industry.
Furthermore, the most targeted industries and businesses are going to be those where standards for security have historically been weak. In particular, industrial manufacturers and distributors—who were especially targeted last year—will suffer from cyber attacks that will hinder their productivity given their dependencies on automation, robotics, and the supply chain as entryways in their networks. Businesses in these industries would be wise to invest in their cyber defences and educate employees to increase cyber security awareness at every level of the organisation.
What this Means for Cyber Incident Response
This year, a strong emphasis will be put on improving security standards for businesses in order to prevent attacks more effectively. Concurrently, government bodies will seek to ensure there is more transparency in cyber incident response, especially regarding ransomware payments—likely instituting bans and limitations for businesses looking to pay criminal groups for decryption keys.
With cyber attacks affecting 1 in 4 users, having a secure cyber incident response plan is now more crucial than ever. Whilst regular patching, security settings management apps, managed detection and response (MDR) software and good cyber hygiene provide a basic level of protection, they are fallible.
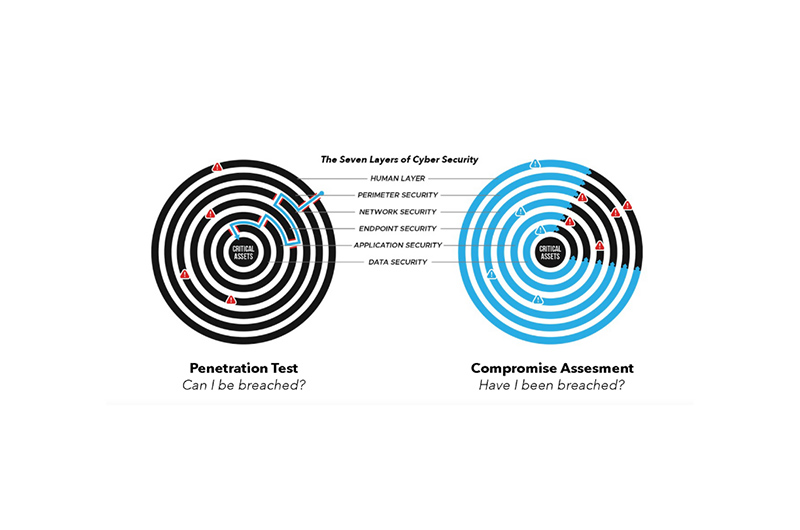
In 2022, having a trusted incident responder on call can make all the difference between surviving a cyber attack with limited losses and having to shut down business because of business interruption, bringing monetary and reputational losses. Blackpanda also recommends running quarterly Compromise Assessments to spot potential malware early and reduce its chances of causing havoc in company networks.
All Blackpanda consulting, compromise assessment, digital forensics, and incident response services are available through pre-paid retainers and specialist cyber insurance providers such as our partners at Pandamatics Underwriting. To learn more about Blackpanda services, reach out to our team here.
IR1: The most effective cyber risk management solution for SMEs in Asia
Waiting for an attack to happen before you contact a cyber incident response team can cost precious time and a high hourly fee, which is why pre-purchasing a retained solution is the best way to optimise response time and minimise costs.
Blackpanda’s IR-1 subscription is the most effective solution for small and medium enterprises in Asia Pacific facing limited resources and knowledge in managing cyber breaches. IR-1 aims to help them manage cyber breaches and mitigate their impact by offering a 12-month subscription plan that includes 24/7 incident response availability, one incident response activation credit, discounted rates for Blackpanda services, and unlimited access to a digital library. IR-1 is staffed by highly trained specialists, and businesses can renew the subscription upon expiry.
Get in touch with us to learn more about IR-1.